Anonymous External Attack.exe
Compilation Time. VT first submission. Anonymous External Attack.exe. 26 antivirus identified as “HackerTool”.
- Anonymous External Attack.exe. 7 2 1 واکنش ها: felanadare ، mamadhack ، vartin و 7 نفر دیگر. به اشتراک گذاری این ارسال.
- Anonymous External Attack is developed by ANONYMOUS AZERBAJAN. The most popular version of this product among our users is 1.0. The product will soon be reviewed by our informers.
- EXE issues related anonymous external attack.exe can be attributed in most cases to executable files that are corrupt, missing, or infected, and often encountered during the Anonymous External Attack software launch phase. Downloading and replacing your EXE file can fix the problem in most cases. In addition, if your anonymous external attack.
- Anonymous External Attack.exe download at 2shared. Click on program Anonymous External Attack.exe to start downloading. 2shared - Online file upload - unlimited free web space. File sharing network. The file ANONYMOUS EXTERNAL ATTACK V1.03.EXE must be deleted from the system immediately.
Introduction
As anyone who tracks attacks on the internet can tell you, Activists using hacking activity, aka 'Hacktivists', have discovered that a relatively basic hacking approach, with buy-in from disenfranchised groups of people, can have significant effects on online businesses.
With names like #OpISIS, #OpParis, #OpMonsanto, #OpWhales, #OpKillingBay, #OpKKK, and #OpTrump, you can easily see that Hacktivists focus their attention on a wide variety of causes.
The 2016 Olympic Games are coming to a close, but we see that they are no different. If there is a major event with significant press coverage, it will typically draw Hacktivist attention.
The modern Olympic Games are considered the foremost sporting event in the world. They are held every four years in different host cities that are chosen by the International Olympic Committee (IOC) and draw the world's attention with millions of spectators around the globe.
This year's event is being held in Rio de Janeiro, Brazil, and is attracting the attention not only of sports fans but also of terrorists and cyber hacktivists.
Anonymous External Attack.exe Indir
Recent terrorist incidents in Belgium, France and other countries, as well as past incidents during Olympic Games like those in Munich in 1972 and Atlanta in 1996 raise concerns about threats at Rio 2016.
Figure 1 - Arrests made for plotting Olympic terror
In addition to threats to the physical safety and security of people and organizations involved in these Olympic Games, cybersecurity is also a real concern.
Hacktivist-related incidents aim to bring attention to several kinds of causes and have increased over the years. Some hacking groups, like Anonymous, have been leading operations and encouraging people to join causes for several years.
Several examples include Anonymous operations #OpNice (Operation 'Nice') to 'hunt' members of the terrorist group responsible for the attack on the French city which killed almost a hundred people, #OpKKK (Operation 'Ku Klux Klan') to reveal the names of up to 1,000 members of the Ku Klux Klan and other affiliated groups, #OpIcarus (Operation 'Icarus') to shut down the banks, and #OpWhales (Operation 'Whales') targeting Iceland and Japan websites against whale slaughter.
A few months ago, before the start of Rio 2016, Anonymous announced another operation called #OpOlympicHacking (Operation 'Olympic Hacking').
Figure 2 - Anonymous #OpOlympicHacking
Motivation
#OpOlympicHacking has social motivation in Brazil as did #OpWorldCup (Operation 'WorldCup'), launched by Anonymous during the 2014 FIFA World Cup held in Brazil which targeted various government organizations as a form of protest against hosting the event.
The Anonymous group released the following statement about #OpOlympicHacking:
'Hello Rio de Janeiro. We know that many have realized how harmful it was (and still is) the Olympic Games in the city. The media sells the illusion that the whole city celebrates and commemorate the reception of tourists from all over the world, many of them attracted by the prostitution network and drugs at a bargain price. This false happiness hides the blood shed in the suburbs of the city, mainly in the favelas thanks to countless police raids and military under the pretext of a fake war. Poverty is spreading throughout the city, forcing entire families to leave their homes and traditional neighborhoods on account of high prices of rent and / or removals made by a corrupt city hall and serves only the wishes of the civil construction. We already manifested in other communications our repudiation to the realization of megaevents in the middle of the glaring social inequalities in this country. Still, even after so many words, so many manifestos or protests on the streets (all always fully supervised by repression, if not repressed with brutal violence) looks like the goverment will continue ignoring the voices of their own people. Therefore, we will continue with our operations to unmask the numerous arbitrary actions of those who are state and therefore its own population enemies.
Two videos have been also published, calling people to join #OpOlympicHacking:
Figure 3 -' #OpOlympicHacking - Let The Games Begin' Youtube video
Figure 4 - 'Exclusion of the Olympic Games' Youtube video
Operation
Anonymous describes itself as 'an internet gathering' with 'a very loose and decentralized command structure that operates on ideas rather than directives.'
The Anonymous Brasil cell is coordinating the #OpOlympicHacking operation by using communication channels like Twitter, Facebook, Youtube and IRC channels.
These channels are used to coordinate DDoS attacks again certain targets and to publicize the results of previous attacks and campaigns, as shown in the examples below:
Figure 5 - Anonymous Brasil Twitter account coordinating the operation
Besides coordinating DDoS attacks against certain targets, these channels are also being used to discuss and encourage people to search for vulnerabilities in the targets.
Figure 6 - IRC #OpOlympicHacking channel
DDoS tool ('opolympddos')
A tool to perform DDoS attacks against certain targets has been especially developed and shared for the #OpOlympicHacking operation.
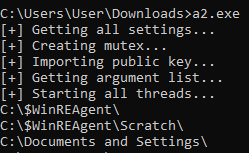
Figure 7 - #OpOlympicHacking DDoS tool executable file
The #OpOlympicHacking DDoS tool, or 'opolympddos', is a set of executable (VB .NET and Python scripts converted to Windows executable files) and batch files. It allows anyone who wants to collaborate on the operation to perform DoS attacks by installing TOR and by clicking pre-configured buttons associated to specific targets, in order to launch Layer 7 DoS attacks against the targets. This is achieved by creating persistent connections and sending HTTP requests with random data and user-agents.
Figure 8 - #OpOlympicHacking DDoS tool main page
Other DDoS Tools
There is evidence that other DDoS tools have also been mentioned and shared among hacktivists to perform DDoS attacks against #OpOlympicHacking targets:
Anonymous External Attack.exe
- A compressed file containing a set of 'hacker tools'. None of these are really new as shown in the table below:

File | Compilation Time | VT first submission | Note |
| Anonymous External Attack.exe | 22/03/12 11:54 | 23/03/12 09:09 | HTTP Attacker. 26 antivirus identified as 'HackerTool' |
| Bull-dosa.exe | 05/11/11 05:59 | 07/12/11 01:56 | DOS Tool. 21 antivirus identified as 'HackerTool' |
| FireFlood.exe | 21/01/12 22:03 | 22/01/12 00:20 | DOS Tool. Possible anti-virtualization techniques. |
| LOIC.exe | 13/12/14 07:09 | 14/12/14 00:57 | DOS Tool with user tracking via google analytics. |
| LOIC 2013.exe | 05/01/13 07:58 | 21/01/13 20:37 | |
| MacStartx User Attack [ tiger ].exe | 26/10/13 06:14 | 25/10/16 11:00 | Tool offered in BR forum: hxxp://www.connect-trojan.net/2014/08/macstartx-user-attack-tiger-v461.html |

Figure 9 - 'Hacker Tools' to perform DDoS attacks
Figure 10 - LOIC tool
Figure 11 - httpdoser Python script shared in #OpOlympicHacking Facebook page
Targets
Anonymous leaders have been sharing a list of potential targets via Pastebin posts. So far, there is evidence that the #OpOlympicHacking operation is targeting the organizations tied to scandal rumors in relation to the Olympics.
Attacks
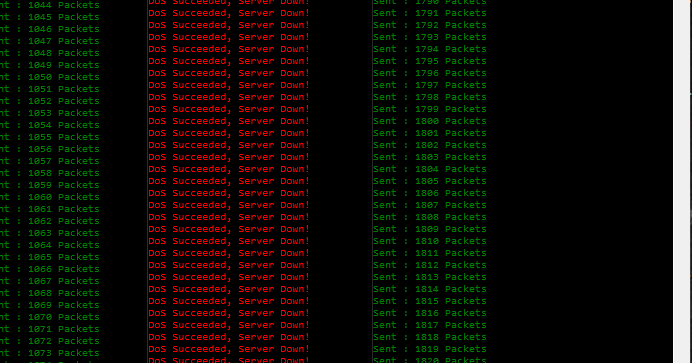
A few websites have been targeted by DDoS and DoX attacks. The websites that Anonymous claims were shut down during the #OpOlympicHacking include sites pertaining to the National and local governments as well as sports organizations.
Figure 12 - Some targets went down after DDoS attacks
Additionally, Anonymous claims that several organizations and people related to the Olympic Games event had sensitive data exposed.
Figure 13 - Databases got hacked and leaked
Conclusion
The volume and frequency of attacks known to date is below what RSA experts had expected and with the majority of them being related to DDOS activity, fairly low tech and of limited longterm impact. RSA researchers are continuing to monitor and identify additional threats. With the conclusion of the Olympics on Sunday, August 21, the volume of #OpOlympicHacking attacks will likely decrease significantly and the next wave of threats may start percolating around the next big event.
Contents
- 1. What is anonymous external attack.exe?
- 2. Is anonymous external attack.exe safe, or is it a virus or malware?
- 3. Can I remove or delete anonymous external attack.exe?
- 4. Common anonymous external attack.exe error messages
- 5. How to fix anonymous external attack.exe
- 6. August 2021 Update
- 7. Download or reinstall anonymous external attack.exe
What is anonymous external attack.exe?
anonymous external attack.exe is an executable file that is part of Anonymous External Attack developed by Microsoft Corporation. The Windows Vista version of the software: 1.0.0.0 is usually about 218112 bytes in size, but the version you have may differ.
The .exe extension of a file name displays an executable file. In some cases, executable files can damage your computer. Please read the following to decide for yourself whether the anonymous external attack.exe file on your computer is a virus or malware that you should delete, or if in fact it is a valid Windows operating system file or reliable application.
Recommended: Identify anonymous external attack.exe related errors
(optional offer for Reimage - Website | EULA | Privacy Policy | Uninstall)
Is anonymous external attack.exe safe, or is it a virus or malware?
The first thing that will help you determine if a particular file is a legitimate Windows process or a virus, is the location of the executable itself. With anonymous external attack.exe for example, it's path will probably be something like C:Program FilesMicrosoft CorporationAnonymous External Attackanonymous external attack.exe
To determine it's path, open Task Manager, go to View -> Select Columns and select 'Image Path Name' to add a location column to your Task Manager. If you find a suspicious directory here, it may be a good idea to investigate this process further.
Another tool that can sometimes help you detect bad processes is Microsoft's Process Explorer. Start the program (it does not require installation) and activate 'Check Legends' under Options. Now go to View -> Select Columns and add 'Verified Signer' as one of the columns.
If the 'Verified Signer' status of a process is listed as 'Unable to Verify', you should take a moment look at the process. Not all good Windows processes have a Verified Signature label, but neither do any of the bad ones.
The most important facts about anonymous external attack.exe:
- Name: anonymous external attack.exe
- Software: Anonymous External Attack
- Publisher: Microsoft Corporation
- Expected Location: C:Program FilesMicrosoft CorporationAnonymous External Attack subfolder
- Expected Full Path: C:Program FilesMicrosoft CorporationAnonymous External Attackanonymous external attack.exe
- SHA1: df4b2644052584f40999b455ceecbb6c3bb37f0c
- SHA256: d5f01c8bae54b9443565bc471fdd56d77b0fe45f2f3238e92d61667f1451c9c4
- MD5: 20e2aa585fc0c9ce6a036ae4f41e988f
- Known to be up to 218112 bytes in size on most Windows;
If you had any difficulties with this executable, you should determine if it's trustworthy before deleting anonymous external attack.exe. To do this, find this process in Task Manager.
Find its location and compare the size etc with the above facts.
If you suspect that you may be infected with a virus, then you must attempt to fix it immediately. To delete the anonymous external attack.exe virus, you must download and install a full security application like this. Note that not all tools can detect every type of malware, so you may need to try several options before you're successful.
In addition, the functionality of the virus may itself affect the deletion of anonymous external attack.exe. In this case, you must enable Safe Mode with Networking - a secure environment that disables most processes and loads only the most required services and drivers. When there, you can run a security program and a complete system analysis.
Can I remove or delete anonymous external attack.exe?
You should not delete a safe executable file without a valid reason, as this may affect the performance of any associated programs that use that file. Be sure to keep your software and programs up to date to avoid future problems caused by corrupted files. With regard to software functionality issues, check driver and software updates more often, so there is little or no risk of such problems occurring.
The best diagnosis for these suspicious files is a complete system analysis with either ASR Pro or this antivirus and malware remover. If the file is classified as malicious, these applications will also delete anonymous external attack.exe and get rid of the associated malware.
However, if it is not a virus and you need to delete anonymous external attack.exe, then you can uninstall Anonymous External Attack from your computer using its uninstaller. If you cannot find it's uninstaller, then you may need to uninstall Anonymous External Attack to completely delete anonymous external attack.exe. You can use the Add/Remove Program function in the Windows Control Panel.
- 1. In the Start menu (for Windows 8, right-click the screen's bottom-left corner), click Control Panel, and then under Programs:
o Windows Vista/7/8.1/10: Click Uninstall a Program.
o Windows XP: Click Add or Remove Programs.
- 2. When you find the program Anonymous External Attack, click it, and then:
o Windows Vista/7/8.1/10: Click Uninstall.
o Windows XP: Click the Remove or Change/Remove tab (to the right of the program).
- 3. Follow the prompts to remove Anonymous External Attack.
Common anonymous external attack.exe error messages
The most common anonymous external attack.exe errors that can appear are:
• 'anonymous external attack.exe Application Error.'
• 'anonymous external attack.exe failed.'
• 'anonymous external attack.exe has encountered a problem and needs to close. We are sorry for the inconvenience.'
• 'anonymous external attack.exe is not a valid Win32 application.'
• 'anonymous external attack.exe is not running.'
• 'anonymous external attack.exe not found.'
• 'Cannot find anonymous external attack.exe.'
• 'Error starting program: anonymous external attack.exe.'
• 'Faulting Application Path: anonymous external attack.exe.'
These .exe error messages can occur during the installation of a program, during the execution of it's associate software program, Anonymous External Attack, during the startup or shutdown of Windows, or even during the installation of the Windows operating system. Keeping a record of when and where your anonymous external attack.exe error occurs is important information when it comes to troubleshooting.
How to fix anonymous external attack.exe
A clean and tidy computer is one of the best ways to avoid problems with anonymous external attack.exe. This means performing malware scans, cleaning your hard disk with cleanmgr and sfc /scannow, uninstalling programs you no longer need, monitoring any auto-start programs (with msconfig), and enabling automatic Windows updates. Don't forget to always make regular backups or at least define recovery points.
If you have a bigger problem, try to remember the last thing you did or the last thing you installed before the problem. Use the resmon command to identify the processes that are causing your problem. Even in case of serious problems, instead of reinstalling Windows, you should try to repair your installation or, in the case of Windows 8, by executing the command DISM.exe /Online /Cleanup-image /Restorehealth. This allows you to repair the operating system without data loss.
To help you analyze the anonymous external attack.exe process on your computer, you may find the following programs useful: Security Task Manager displays all Windows tasks running, including built-in hidden processes such as keyboard and browser monitoring or auto-start entries. A single security risk rating indicates the probability that it is spyware, malware or a potential Trojan horse. This anti-virus detects and removes spyware, adware, Trojans, keyloggers, malware and trackers from your hard disk.
Updated August 2021:
We recommend you try using this new tool. It fixes a wide range of computer errors, as well as protecting against things like file loss, malware, hardware failures and optimizes your PC for maximum performance. It fixed our PC quicker than doing it manually:
- Step 1 : Download PC Repair & Optimizer Tool (Windows 10, 8, 7, XP, Vista – Microsoft Gold Certified).
- Step 2 : Click “Start Scan” to find Windows registry issues that could be causing PC problems.
- Step 3 : Click “Repair All” to fix all issues.
(optional offer for Reimage - Website | EULA | Privacy Policy | Uninstall)
Download or reinstall anonymous external attack.exe
It is not recommended to download replacement exe files from any download sites, as these may themselves contain viruses etc. If you need to download or reinstall anonymous external attack.exe, then we recommend that you reinstall the main application associated with it Anonymous External Attack.
What is Anonymous External Attack
Overview of Anonymous external attack.exe Anonymous external attack.exe is a type of EXE file associated with Anonymous External Attack developed by Microsoft Corporation for the Windows Operating System.
Operating system information
anonymous external attack.exe errors can occur in any of the following Microsoft Windows operating systems:
- Windows 10
- Windows 8.1
- Windows 7
- Windows Vista
- Windows XP
- Windows ME
- Windows 2000
RECOMMENDED: Click here to troubleshoot Windows errors and optimize system performance