Hydra Hack
This is the write up for the room Hydra on Tryhackme and it is part of the CompTIA Pentest+ Path. Make connection with VPN or use the attackbox on Tryhackme site to connect to the Tryhackme lab environment. Many modules use this, a few require it! To see the special option of a module, type: hydra -U e.g./hydra -U http-post-form The special options can be passed via the -m parameter, as 3rd command line option or in the service://target/option format.
Hydra is a parallelized login cracker which supports numerous protocols to attack. It is very fast and flexible, and new modules are easy to add.This tool makes it possible for researchers and security consultants to show how easy it would be to gain unauthorized access to a system remotely.
Hydra supports: Cisco AAA, Cisco auth, Cisco enable, CVS, FTP, HTTP(S)-FORM-GET, HTTP(S)-FORM-POST, HTTP(S)-GET, HTTP(S)-HEAD, HTTP-Proxy, ICQ, IMAP, IRC, LDAP, MS-SQL, MySQL, NNTP, Oracle Listener, Oracle SID, PC-Anywhere, PC-NFS, POP3, PostgreSQL, RDP, Rexec, Rlogin, Rsh, SIP, SMB(NT), SMTP, SMTP Enum, SNMP v1+v2+v3, SOCKS5, SSH (v1 and v2), SSHKEY, Subversion, Teamspeak (TS2), Telnet, VMware-Auth, VNC and XMPP.
Hydra works in 4 modes:
- One username & one password
- User-list & One password
- One username & Password list
- User-list & Password list
Hydra Hacker
The screenshot of the command is following:
If we want to make custom wordlists then we can use crunch.

For a ftp login in our localhost we can use following command:
The screenshot is following:
Then the command will be like following:
hydra -L /path/of/usernames.txt -P /path/of/pasword.txt ftp://192.168.1.1
In the way of cybersecurity after scanning with nmap if we find ftp port is open then we can try hydra to bruteforce the ftp login.
xHydra - Hydra with graphical interface
There is a graphical version of hydra, it's called xHydra. It is also comes pre-installed in our Kali Linux machine.
You can open xHydra from the Kali Linux terminal by using xhydra command:
This command will open the xhydra as we can see in the following screenshot:
- Target - Specify the target
- Passwords – Specify password options & wordlists
- Tuning – Specify how fast should hydra work. Other timing options also available.
- Specific – For testing on specific targets like a domain, https proxy etc.
- Start – Start and Stop the attack & shows the output.
For more tutorials like this visit our website regularly and for quick updates follow us on Twitter.
For any kind of problem or suggestion comment down we always replay.
Introduction
You think your passwords are strong and secure? You are mistaken! There are numerous options to secure your password, but when it comes to the Password Cracker THC Hydra, you are done. However, you can use some of the cryptography techniques to secure your password or at least make it difficult to crack.
It’s very important to mention that this tool is just proof of concept, which gives researchers and security teams the ability to see how they can protect themselves against such attacks.
Password Cracker THC Hydra
Hydra is a parallelized password cracker which supports numerous protocols to attack. It is very fast and flexible, and new modules are easy to add. This tool makes it possible for researchers and security consultants to show how easy it would be to gain unauthorized access to a system remotely.
You will often come across information that indicates that the hydra is one of the fastest network logon crackers, also you’ll see that hydra supports multiple protocol attacks, unlike other hackers tool.
Hydra supports the following protocols:
- Asterisk, AFP, Cisco AAA, Cisco auth, Cisco enable, CVS, Firebird, FTP,
- HTTP-FORM-GET, HTTP-FORM-POST, HTTP-GET, HTTP-HEAD, HTTP-POST,
- HTTP-PROXY, HTTPS-FORM-GET, HTTPS-FORM-POST, HTTPS-GET, HTTPS-HEAD,
- HTTPS-POST, HTTP-Proxy, ICQ, IMAP, IRC, LDAP, MS-SQL, MYSQL, NCP, NNTP,
- Oracle Listener, Oracle SID, Oracle, PC-Anywhere, PCNFS, POP3, POSTGRES, RDP,Rexec,
- Rlogin, Rsh, RTSP, SAP/R3, SIP, SMB, SMTP, SMTP Enum, SNMP v1+v2+v3,SOCKS5,
- SSH (v1 and v2), SSHKEY, Subversion, Teamspeak (TS2), Telnet, VMware-Auth, VNC and XMPP.
Install THC Hydra
The first step is to download and compile THC-Hydra (clean compile tested on Linux, Windows/Cygwin, Solaris, FreeBSD/OpenBSD, QNX (Blackberry 10) and MacOS).
Install hydra with the following commands:
Note: For ssh module, you need to setup libssh (*not libssh2!) and for ssh v1 support, just add -DWITH_SSH1=On option in the cmake command line.
In order to install required libraries (xhydra), Ubuntu/Debian users need to run:

Exception:
- Oracle, SAP R/3 and Apple Logging Protocols modules – you’ll need to download and install them from appropriate sources;
- Other Linux derivates /BSD based systems – use the system software installer and find adequate libraries;
- Other – download & install source libraries and compile them manually.
THC Hydra Commands
- type .
/hydra -htoo see all available command line options or hydrafor a shorter version.
- –
Vvrebose mode - –
llogin name - –
P<password_file/wordlist> - –
ensr, additional checks, “n” for null password, “s” try login as pass, “r” try the reverse login as pass - –
t<number of paralel connects> - –
w<max time to wait for response> - –
f: exit after first login/password pair found - –
m: OPTIONS – module specific options. See hydra -U <module> what options are available.
Hydra Password Cracker Examples
HTTP-POST-FORM:
- http-post-form : supported service
- login_error: grep text from HTML form if login failed
- log: form username input field name
- pwd: form password input field name
FTP Example (WordList):
SSH Example(WordList):
Telnet Example (WordList):
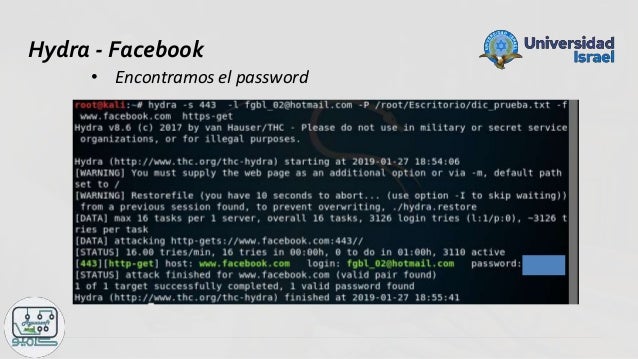
HTTP Login Example (WordList). For HTTPS set “https-get”:
RDP Example (WordList):
MySQL Example (WordList):
Restore Aborted Session

Hydra Hack
hydra.restore file contains all necessary information for the session restore, which is written every 5 min. So, if hydra crashes or you just abort it with Control + C, you’ll find all information in that file. NOTE: you can’t copy the hydra.restore file to different platforms.
Hydra Hack Client Download
Scan/Crack Over a Proxy
Hydra Hacked Minecraft Client
The environment variable HYDRA_PROXY_HTTP defines the web proxy (*this works just for the http/www service!). Use the following syntax:
You can use the HYDRA_PROXY variable to scan/crack for all other services with the same syntax:
Interested in Network Scanning? Check out ZMap: Fast Internet Scanner.