Sql Injection Tool Get Cc Cvv
- Sql Injection Tool Get Cc Cvv Online
- Sql Injection Tool Get Cc-cvv
- Sql Injection Tool Get Cc Cvv Download
- Sql Injection Tool Get Cc Cvv Free
- Sql Injection Tool Get Cc Cvv File

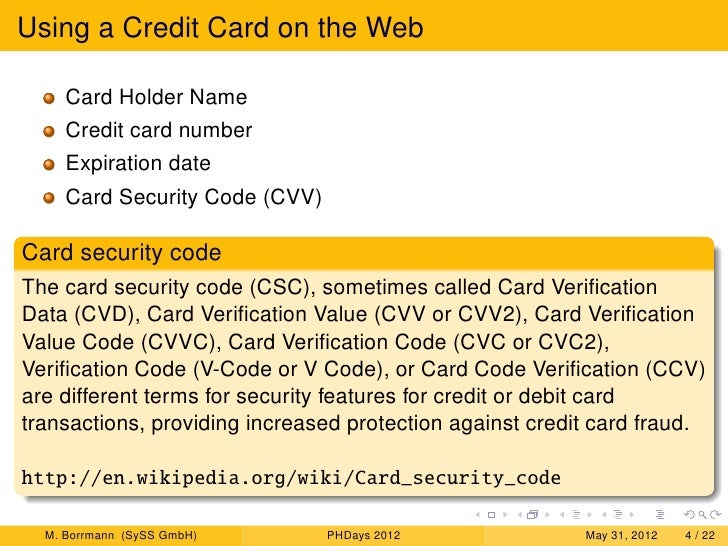
The OWASP ZAP tool was created to help users automatically detect security vulnerabilities in web applications while developing and testing them.
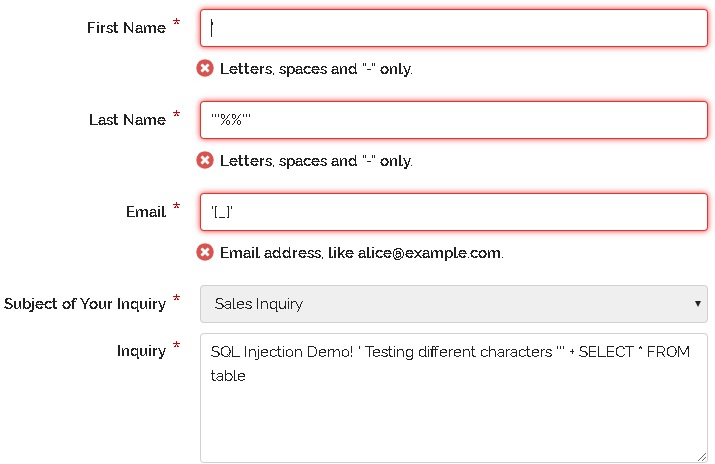
The tool can do an SQL Injection test by inserting special characters (eg. ', ', 2*3) in all input fields of the target application and monitoring the web page's behavior. If database errors are discovered on the website, this could be the scenario of an SQL Injection attack.
To validate the vulnerability found, the SQL Injection scanner attempts to construct a syntactically correct SQL query that demonstrates the injection was successful. That is why the following results will be displayed:
http://vulnapp.example.com/bookings.php?cat=4 AND 1=1 -- The SQL Injection scanner does not attempt to exploit SQL injection, it simply detects the presence of any vulnerability that could affect your backend database. If flaws are detected, our online tool offers detailed information about the risks you are exposed to and recommendations on how to perform an effective remediation process. Start scanning for web applications vulnerabilities today so you will not be exposed to SQL Injection attacks which let hackers get to tamper with sensitive information (such as usernames, passwords, and other essential credentials) by disclosing, or deleting it.
For more in-depth information about the SQL Injection attacks, including solutions on how to remediate this vulnerability, you can found on the OWASP SQL Injection Page.
Overview
Sql Injection Tool Get Cc Cvv Online
A SQL injection attack consists of insertionor “injection” of a SQL query via the input data from the client to theapplication. A successful SQL injection exploit can read sensitive datafrom the database, modify database data (Insert/Update/Delete), executeadministration operations on the database (such as shutdown the DBMS),recover the content of a given file present on the DBMS file system andin some cases issue commands to the operating system. SQL injectionattacks are a type of injection attack, in which SQL commandsare injected into for itemName, then the query becomes the following:
This article is based on our previous article where you have learned different techniques to perform SQL injection manually using dhakkan. Today we are again performing SQL injection manually on a live website “vulnweb.com” in order to reduce your stress of installing setup of dhakkan. Exploiting SQL Injection: a Hands-on Example. In this series, we will be showing step-by-step examples of common attacks. We will start off with a basic SQL Injection attack directed at a web application and leading to privilege escalation to OS root. SQL Injection is one of the most dangerous vulnerabilities a web application can be prone to.
The addition of the OR 'a'='a' condition causes the where clause toalways evaluate to true, so the query becomes logically equivalent tothe much simpler query:
SELECT * FROM items;
This simplification of the query allows the attacker to bypass therequirement that the query only return items owned by the authenticateduser; the query now returns all entries stored in the items table,regardless of their specified owner.
Sql Injection Tool Get Cc-cvv
Example 3
This example examines the effects of a different malicious value passedto the query constructed and executed in Example 1. If an attacker withthe user name hacker enters the string 'name'); DELETE FROM items; --'for itemName, then the query becomes the following two queries:
Many database servers, including Microsoft® SQL Server 2000, allowmultiple SQL statements separated by semicolons to be executed at once.While this attack string results in an error in Oracle and otherdatabase servers that do not allow the batch-execution of statementsseparated by semicolons, in databases that do allow batch execution,this type of attack allows the attacker to execute arbitrary commandsagainst the database.
Notice the trailing pair of hyphens (--), which specifies to most database servers that the remainder of the statement is to be treated asa comment and not executed. In this case the comment character serves to remove the trailing single-quote left over from the modified query. In adatabase where comments are not allowed to be used in this way, the general attack could still be made effective using a trick similar tothe one shown in Example 1. If an attacker enters the string 'name'); DELETE FROM items; SELECT * FROM items WHERE 'a'='a', the followingthree valid statements will be created:
One traditional approach to preventing SQL injection attacks is tohandle them as an input validation problem and either accept onlycharacters from an allow list of safe values or identify and escape adeny list of potentially malicious values. An allow list can be a veryeffective means of enforcing strict input validation rules, butparameterized SQL statements require less maintenance and can offer moreguarantees with respect to security. As is almost always the case,deny listing is riddled with loopholes that make it ineffective atpreventing SQL injection attacks. For example, attackers can:
- Target fields that are not quoted
- Find ways to bypass the need for certain escaped meta-characters
- Use stored procedures to hide the injected meta-characters
Sql Injection Tool Get Cc Cvv Download
Manually escaping characters in input to SQL queries can help, but itwill not make your application secure from SQL injection attacks.
Sql Injection Tool Get Cc Cvv Free
Another solution commonly proposed for dealing with SQL injectionattacks is to use stored procedures. Although stored procedures preventsome types of SQL injection attacks, they fail to protect against manyothers. For example, the following PL/SQL procedure is vulnerable to thesame SQL injection attack shown in the first example.
Stored procedures typically help prevent SQL injection attacks bylimiting the types of statements that can be passed to their parameters.However, there are many ways around the limitations and many interestingstatements that can still be passed to stored procedures. Again, storedprocedures can prevent some exploits, but they will not make yourapplication secure against SQL injection attacks.

Sql Injection Tool Get Cc Cvv File
Related Attacks
References
- SQL Injection Knowledge Base - A reference guide for MySQL, MSSQL and Oracle SQL Injection attacks.
- GreenSQL Open Source SQL Injection Filter - An Open Source database firewall used to protect databases from SQL injection attacks.
- An Introduction to SQL Injection Attacks for Oracle Developers
- This also includes recommended defenses.