Telegram Thc Hydra
(Please note this post was published last 4th february 2013 in the Spanish version of Security Art Work. See original post: THC-Hydra: Obtener credenciales de usuario por fuerza bruta)
Jun 18, 2011 THC-HYDRA v6.4 - Fast network logon cracker THC-HYDRA is a very fast network logon cracker which support many different services. This tool is a proof of concept code, to give researchers and security consultants the possibility to show how easy it would be to gain unauthorized access from remote to a system. View Telegram channel's statistics 'HYDRA REBORN//HIAT' - @hydrareborn. Subscribers, subscribers gained, views per day, forwards and other analytics at the Telegram Analytics website. Essentially THC Hydra is a fast and stable Network Login Hacking Tool that will use a dictionary or brute-force attacks to try various passwords and login combinations against a login page. This hacking tool supports a wide set of protocols including Mail (POP3, IMAP, etc.) and databases such as LDAP, SMB, VNC, and SSH. Using THC hydra or similar to crack a password in a URL? Hi guys, so I've got a login I was trying to crack for a bit of fun, although it now frustrating me so I've come here! I've got a URL like this.
THC-Hydra is a software used to crack login systems of different services such as HTTP, FTP, TELNET, IMAP, SMB, SSH, etc. in a very easy and fast way. Its latest version (7.4.2) was released last 7th January.
This tool has earned a great reputation thanks to its console mode both in Linux and Windows systems (also offering Linux users the option to use a graphical interface) and the possibility to execute the attacks using threads, giving the user the option to choose the number of threads used to perform the attack.
To carry out the attacks, THC-Hydra is based on the use of dictionaries that contain all the possible options the user may want to try. These are completely necessary for the execution of the program to keep trying different possibilities and to obtain the user credentials.
Its basic version from the command line is very simple: just set the host we want to attack, the type of service, the files that contain the user and password values, and the characteristics of the protocol (when necessary).
For instance, to attack an FTP service, you need: the host to be analyzed, the type of service (ftp), the file containing the list of users (option -L) and the file containing the password list (option -P), what results in:
A more specific example could be an attack against the HTTP login of a website that sends the data using the POST method. In this case in addition to the above information, the user will need to specify the exact URL of the login form, the name of the user and password values in the web form, and the string of HTML code to indicate whether it was successful or not (based on the response from the server). For this example, the command would be as follows:
Where the exact url of the form is “login.php“, the parameter name of the form containing the user is “var_user“, the password is “var_pass” and the string that indicates that the login is correct is “Login successful“.
In the next picture we see the application output with the different users and passwords that the tool finds in the login form HTTP using POST method:
It should be noted that these are not the only options that can be set in the tool. It is possible to specify the number of threads used (option -t), carry out the attack with a given user (option -l) or a specific password (option -p), add cookies (C=cookie_value), add headers (H=header value), etc. It is strongly recommended to analyze the different options shown in the program help (option -h), the different examples and help links offered on their website http://www.thc.org/thc-hydra/.
Finally, thanks to tools like THC-Hydra, we can see how easy it can be to get a list of users using passwords too obvious and/or common. This once again demonstrates the importance of using strong passwords for those services we use.
A very fast network logon cracker with thc-hydra dictionary attack tool that supports many different services. You can use the thc-hydra tool to crack a password Many hackers love this tool due to its GUI and Cmdline interface.
If you are new to ethical hacking and don’t know how to use thc-hydra, you can still use it easily due to the GUI interface.
Dictionary attack tool thc-hydra Description:
According to the official website of thc-hydra, the biggest security holes are passwords, as every password security study shows. The device is a proof of concept code to show researchers and security consultants the possibility to demonstrate how easy it would be to gain unauthorized access from remote and various online services.
Note: THIS TOOL IS FOR LEGAL PURPOSES ONLY! ( crack password )
There are already several login hacker tools available, however none does Either support more than one protocol to attack or support panellized Connects.
Protocols supported by thc-hydra
Asterisk, AFP, Cisco AAA, Cisco auth, Cisco enable, CVS, Firebird, FTP, HTTP-FORM-GET, HTTP-FORM-POST, HTTP-GET, HTTP-HEAD, HTTP-PROXY, HTTPS-FORM-GET, HTTPS-FORM-POST, HTTPS-GET, HTTPS-HEAD, HTTP-Proxy, ICQ, IMAP, IRC, LDAP, MS-SQL, MYSQL, NCP, NNTP, Oracle Listener, Oracle SID, Oracle, PC-Anywhere, PCNFS, POP3, POSTGRES, RDP, Rexec, Rlogin, Rsh, SAP/R3, SIP, SMB, SMTP, SMTP Enum, SNMP v1+v2+v3, SOCKS5, SSH (v1 and v2), SSHKEY, Subversion, Teamspeak (TS2), Telnet, VMware-Auth, VNC, and XMPP.
How to use hydra in Kali Linux or crack password
Thc-hydra is available in Kali Linux already you don’t need to install or configure it. In Kali Linux hydra available in two-mode Graphical and Command line.
Graphical Interface of Hydra in Kali Linux:
The graphical interface is easy to use so let’s look on the graphical interface of hydra:
Step 1: Open hydra-gtk Go Application > Password attacks>Online Attacks > Hydra-Gtk
Step 2: Configure Hydra for Attack
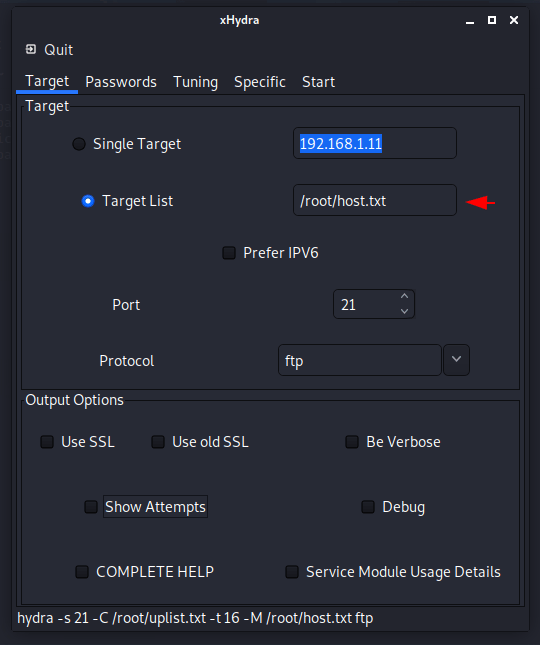
Step 3: Set Target there are the following option is available:
- Single Target: Give the IP address of Single target
- Target List: you can upload the file consist targets list.
- Define Port: specify the port
- Protocol: Select protocol for attack
Step 4: Passwords In this tab you set the username and password and more…
- Username: Give the username if you know
- Username list: if you don’t know the username provide file location consist multiple usernames
- Password: This option for single password
- Password List: Here you provide the wordlist location
- Check on try login as password
- Check on Try empty password
- Check on Try reversed login
Thc Hydra Download For Windows
Step 5: Tuning:- Following options for this tab:
- Number Task: Repeat task
- Time out: configure timeout on not response
- Proxy: Set proxy if you are using. Or leave by default No proxy
Specific: Leave default
Start: Here you can start stop attack and save result
Command line Interface of Hydra in Kali Linux:
As in Linux command line have their own importance and value and most of tools are available with command line interface for linux, Hydra is one of them. to know more about the hydra just execute following command
#Hydra –h
This command will show all options used with hydra command.
You have many options on how to attack with logins and passwords
With -l for login and -p for password you tell hydra that this is the only
login and/or password to try.
With -L for logins and -P for passwords you supply text files with entries.
e.g.:

hydra -l admin -p password ftp://localhost/
hydra -L default_logins.txt -p test ftp://localhost/
hydra -l admin -P common_passwords.txt ftp://localhost/
hydra -L logins.txt -P passwords.txt ftp://localhost/
Additionally, you can try passwords based on the login via the “-e” option.
The “-e” option has three parameters:
s – try the login as password
n – try an empty password
Telegram Thc Hydra Juice
r – reverse the login and try it as password
If you want to, e.g. try “try login as password and “empty password”, you
specify “-e sn” on the command line
Telegram Thc Hydra Powder
Source: https://www.thc.org